Les points de terminaison nécessitent une surveillance continue pour bloquer les attaques les plus récentes.
Barracuda Managed XDR vient compléter un centre d'opérations de sécurité (SOC) mondial fonctionnant 24 h/24, 7 j/7 et 365 jours par an pour assurer une cyberhygiène essentielle et une détection et une réponse rapides aux menaces.
- Défendez-vous contre les menaces qui pourraient voler, modifier, chiffrer ou détruire des données.
- Garantissez la conformité et répondez aux exigences de cyberassurance grâce à une journalisation et une surveillance permanentes.
- Faites bénéficier votre entreprise de talents en cybersécurité rentables et hautement qualifiés.
Fonctionnement
Détection
Agir
Récupérer
La détection précoce est essentielle.
- Exécution de ransomware
- Mauvaise utilisation de l'application
- exécution du code distant
- Attaques sans fichier
- Minage de cryptomonnaie
- Activité du shell de commande
Exécution de ransomware
En plus de détecter les ransomwares connus par des méthodes basées sur les signatures, l'exécution en temps réel est identifiée grâce à des analyses comportementales avancées et à l'IA. Par exemple, XDR Managed Endpoint Security détecte le chiffrement non autorisé de fichiers, la désactivation des fonctionnalités de sécurité et la création de fichiers inhabituels. Grâce à ces informations, il peut détecter les ransomwares, bloquer leur exécution et même revenir en arrière sur les modifications si elles sont détectées après l'activité initiale.
Mauvaise utilisation de l'application
Le moteur d'IA comportementale de XDR Managed Endpoint Security, qui n'est pas limité par l'exigence d'analyse dans le cloud, surveille en temps réel les processus au niveau du noyau pour identifier la mauvaise utilisation de l'application, y compris l'élévation des privilèges, les attaques sans fichier et l'exécution non autorisée de scripts.
Même si le comportement est nouveau, l'apprentissage automatique et les données historiques permettent de distinguer les activités légitimes des utilisations malveillantes. Il offre aux analystes du centre des opérations de sécurité de XDR une vue d'ensemble visuelle et contextuelle des processus et actions associés, permettant la détection des abus et l'amélioration de la réponse aux incidents.
exécution du code distant
XDR Managed Endpoint Security détecte et arrête les attaques par exécution de code à distance (RCE) en surveillant en permanence les processus au niveau du noyau. Le moteur d'IA comportementale peut identifier des irrégularités possiblement indicatrices de tentatives d'exécution de code à distance, telles que l'exécution de code non autorisée. Les activités malveillantes sont rapidement détectées et éliminées.
Attaques sans fichier
Au lieu d'une analyse conventionnelle basée sur les fichiers, XDR Managed Endpoint Security utilise des techniques sophistiquées d'IA comportementale pour détecter les attaques sans fichier en surveillant l'activité malveillante en mémoire. Nous examinons les exécutions de scripts, les processus et les activités inhabituelles qui s'écartent des modèles typiques afin de détecter et d'arrêter les processus malveillants.
Minage de cryptomonnaie
Les capacités d'apprentissage automatique identifient les schémas comportementaux anormaux cohérents avec l'activité de minage. La surveillance en temps réel détecte les actions indiquant une activité de minage de crypto-monnaie non autorisée, telles que les connexions à des pools de minage connus, la consommation excessive de ressources et l'arrêt de processus concurrents sur un système. Les processus malveillants sont automatiquement arrêtés avant qu'ils ne causent de graves dommages.
Activité du shell de commande
L'activité de l'invite de commandes est identifiée à l'aide d'une analyse heuristique et comportementale qui signale une utilisation malveillante ou non autorisée du shell, comme des opérations inhabituelles sur la ligne de commande, des scripts ou des actions administratives. Grâce aux règles de détection propriétaires de Barracuda, XDR Managed Endpoint Security vérifie des actions telles que l'exécution de scripts en mémoire, le contournement des mesures de sécurité ou le déclenchement de modifications non autorisées du système.
La réponse automatisée réduit l'impact des menaces.
Évaluez et atténuez rapidement les menaces potentielles.
Rebondissez rapidement après les incidents de cybersécurité pour limiter les dégâts causés à vos activités.
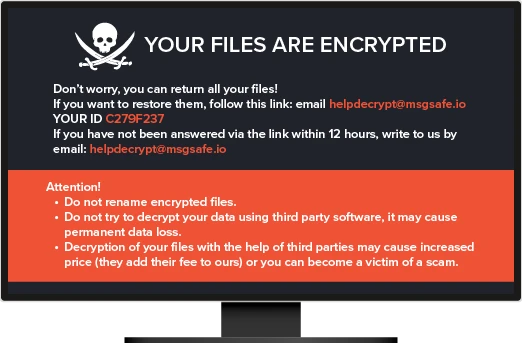
Découvrez comment annuler rapidement les modifications du système causées par un ransomware.
La protection des points de terminaison fait partie d'une suite Managed XDR complète.
Déployez Endpoint Protection seul ou étendez votre protection pour inclure les serveurs, la sécurité du réseau, la sécurité des e-mails, et la sécurité cloud. Adaptez votre stratégie de cybersécurité pour qu'elle s'aligne parfaitement avec les besoins uniques de votre organisation et restez en avance dans le paysage numérique en constante évolution.